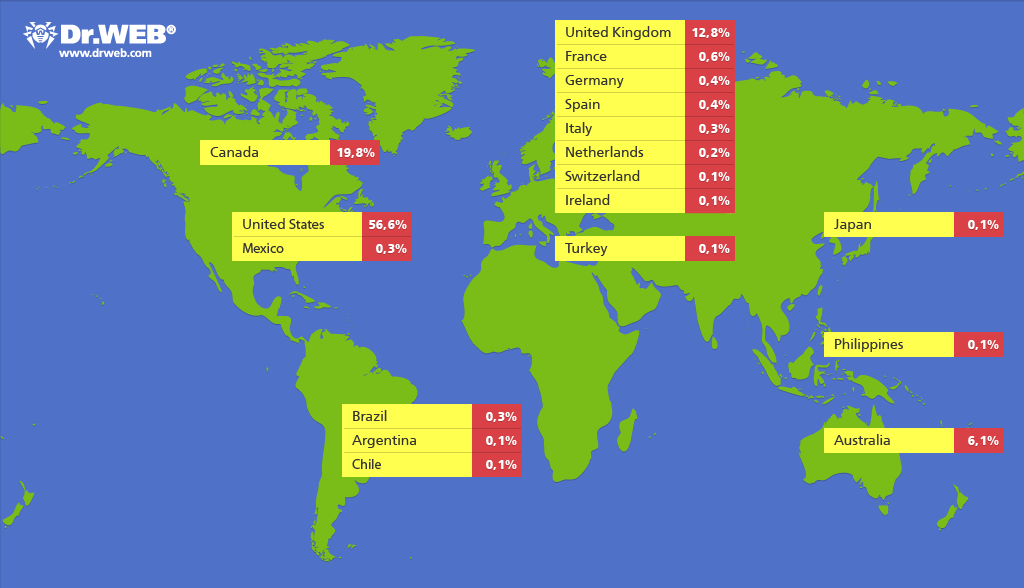
Tuesday, September 17, 2013
New Mac Trojan Discovered Related to Syria
Monday, October 15, 2012
Friday, April 6, 2012
Russian Security Experts Analyze Backdoor.Flashback.39
Security experts have found that even after Apple patched the flaw, the cybercriminals behind the operation didn't seem to be discouraged.
Researchers from Russian security firm Doctor Web analyzed the malicious element and determined that the infection begins when users are redirected to shady sites from compromised domains.
A piece of JavaScript code, placed on websites such as godofwar3.rr.nu, ironmanvideo.rr.nu, killaoftime.rr.nu, or gangstasparadise.rr.nu, loads the Java applet that contains the exploit.
The exploit then saves an executable onto the infected Mac machine. This executable file connects to a remote server from which it downloads and executes the final payload.
Continue Reading
Thursday, November 4, 2010
Mac OS X Boonana Trojan Horse trojan.osx.boonana.a
Continue reading the SecureMac Security Bulletin
Tuesday, November 2, 2010
Yes, you need anti-virus on your Mac.. and now it’s free | Naked Security
Sophos has today announced the world's first free business-strength anti-virus program for home Macs. As Apple computers grow more popular than ever, they're an increasingly-enticing target for hackers (Windows users are still the number one target). And these hackers aren't just mischief-makers—by targeting your computer or applications you use, these criminals are out to steal and profit from your valuable personal information. Don't let them. Get Sophos Anti-Virus Home Edition for the Mac free today.
Thursday, September 23, 2010
Beleaguered Windows users take heart Microsoft just tossed you a bone!
Microsoft Security Essentials has won a lot of praise since its introduction last year. The anti-malware software is unobtrusive and reasonably effective, and its price—free—can't be beat. One fly in the ointment has been the software's licensing terms; MSE is only licensed for home users. Businesses have to look elsewhere for their anti-malware needs.
That's set to change, at least a little, next month. From early October, small businesses—defined here as those with ten PCs or fewer—can use MSE, too. Microsoft claims that enterprise security software is too expensive, complicated, and hard to use for these organizations, hence its decision to expand the reach of MSE.
Read the full story by Peter Bright
Tuesday, June 1, 2010
OSX/OpinionSpy Spyware Installed by Freely Distributed Mac Applications

OSX/OpinionSpy is installed by a number of applications and screen savers that are distributed on sites such as MacUpdate, VersionTracker and Softpedia. The spyware itself is not contained in these applications, but is downloaded during the installation process. This shows the need for an up-to-date anti-malware program with a real-time scanner that can detect this malware when it is downloaded by the original application’s installer.
The information provided with some of these applications contains a misleading text that users must accept explaining that a “market research” program is installed with them, but not all of these specify this. Some of these programs are also distributed directly from developers’ web sites with no such warning.
The malware, a version of which has existed for Windows since 2008, claims to collect browsing and purchasing information that is used in market reports. However, this program goes much further, performing a number of insidious actions, which have led Intego to classify it as spyware.
For full technical details about OSX/OpinionSpy please visit the Intergo web site.
Thursday, January 28, 2010
Attention Members of the dark side. The Evil emperor has given you a gift
Monday, November 23, 2009
iPhone worm can act like botnet say experts
It is specifically targeting people in the Netherlands who are using their iPhones for internet banking with Dutch online bank ING.
It redirects the bank's customers to a lookalike site with a log-in screen.
The worm attacks "jail-broken" phones - a modification which enables the user to run non-Apple approved software on their handset.
The handsets at risk also have SSH (secure shell) installed.
Read the full story at BBC News
More:
Symantec Spots Worm Targeting Jailbroken Apple iPhone Phones
Thursday, November 5, 2009
Windows 7 vulnerable to 8 out of 10 viruses
SophosLabs and loaded a full release copy of Windows 7 on a clean machine. We configured it to follow the system defaults for User Account Control (UAC) and did not load any anti-virus software. Unfortunately, despite Microsoft's claims, Windows 7 disappointed just like earlier versions of Windows.
Saturday, October 17, 2009
Fake antivirus attacks PCs with ransom demand
The Fake antivirus phenomenon has taken an unpleasant turn with the discovery of a Windows program that not only cons users into buying an unnecessary license but appears to lock files and applications on the victim's PC.
According to security company Panda Security, rogueware program Total Security 2009 starts out in conventional fashion with the 'discovery' of a non-existent malware infection for which it demands an unusually ambitious $79.95 (£50), and even has the cheek to ask a further $19.95 for 'premium' technical support.
Read the full story by John E. Dunn , TechWorld
Wednesday, September 30, 2009
First look: Microsoft Security Essentials impresses
After a short three-month beta program, Microsoft is officially releasing Microsoft Security Essentials (MSE), its free, real-time consumer antimalware solution for fighting viruses, spyware, rootkits, and Trojans. MSE is yet another layer of defense the company is offering to help its customers fight the threats that plague Windows PCs.
Microsoft Security Essentials is available for Windows XP 32-bit (8.61MB), Windows Vista/7 32-bit (4.28MB), and Windows Vista/7 64-bit (4.71MB). The final build number is 1.0.1611.0. Microsoft warns that MSE should not be installed alongside any other antimalware application. Indeed, MSE's installer disables Windows Defender completely, which makes sense as it is a sort of superset to Windows Defender. It builds upon Windows Defender by offering both real-time protection and on-demand scanning for all types of malware."
Monday, August 31, 2009
Danger. Your Mac can be hacked. Again. How?
Saturday, August 15, 2009
New Mac OS X DNS changer spreads through social engineering
TrendMicro is reporting on a newly discovered4th member of the OSX_JAHLAV malware family.
The latest variant is once again relying on social engineering, this time spreading under a QuickTime Player update (QuickTimeUpdate.dmg) with a DNS changer component enabling the malware authors to redirect and monitor the traffic of the victim.
More info on OSX_JAHLAV.D:
The Trojan contains component files detected as UNIX_JAHLAV.D and obfuscated scripts detected as PERL_JAHLAV.F. The Perl script then downloads a file from a malicious site and stores it as /tmp/{random 3 numbers}, detected as UNIX_DNSCHAN.AA, which allows a malicious user to monitor the affected user’s activities. This may also cause the user to be redirected to phishing sites or sites where other malware may be downloaded from.
Not only are cybercriminals beginning to acknowledge the “under-served” Mac OS X segment, but also, they’re already borrowing tricks from the Microsoft Windows playbook such as OS-independent tactics like fake codecs and bogus video players. The irony? Both the Mac OS X and Windows malware are hosted on the same domains, with copies of each served on the basis on browser detection.
Read the full story at ZDNet by Dancho Danchev
Still for security, you can't beat Mac OS X because we know of well over 236,000 malicious malware items. These are mostly meant for the MS-Windows environment. Only about 700 are meant for the various Unix/Linux distributions. Current known Mac OSX malware count is even less with 20, so pretty much non-existent at the moment.
Friday, July 31, 2009
iPhone Virus: What You Need to Know
"The iPhone's security flaws were laid bare at the Black Hat Conference in Las Vegas yesterday, and now the smartphone-clutching public has boiled itself into a frenzy. But how serious is this supposed iPhone virus, and what can be done to protect your iPhone from infection? Here is what we know, and why you probably shouldn't worry.
The Attack Comes Through SMS
The iPhone virus exploits a memory corruption bug in the way the iPhone handles SMS messages. If your phone is the target of a hacker, you will receive a text message with only a square in the message -- that's when you know someone is digging his heels into your sand. But according to Eric Everson, founder of security firm MyMobiSafe, it takes a total of 512 text messages to actually get under the hood. The other 511 may float in like ghosts, totally undetectable to the user, but if at least one of them is deleted, the hack is incomplete. Turning your iPhone off or sliding it into Airplane Mode are quick and simple ways to escape the bull's-eye."
Continue Reading reading the full story by Brennon Slattery at PC World
UPDATE: You can now download the fix for this from iTunes
Saturday, June 13, 2009
Look Ma, I created a botnet!
In less than an hour on Thursday, I was able to use programs readily available on the Internet underground for as little as $300 to infect several Windows clients and take complete control of them in a test environment.
In contrast to the real world, the McAfee Malware Experience event, which was akin to a Malware 101 class (or, in my case, Malware for Dummies), served up printed step-by-step instructions for us nonhacker journalists. But McAfee researchers said the programs used--real samples of malicious code from the wild--were not particularly sophisticated and any script kiddie could manage them easily."
Read the full story by Elinor Mills
Friday, May 29, 2009
Gumblar" Computer Virus A Growing Threat
"The Web site compromise attack known as Gumblar has added new domain names that are downloading malware onto unsuspecting computers, stealing FTP credentials to compromise more sites, and tampering with Web traffic, a security firm said on Thursday.
The Gumblar attack started in March with Web sites being compromised and attack code hidden on them. Originally, the malware downloaded onto computers accessing those sites came from the gumblar.cn domain, a Chinese domain associated with Russian and Latvian IP addresses that were delivering code from servers in the U.K."
"Gumblar" Computer Virus A Growing Threat - CBS News
Shared via AddThis
Saturday, April 18, 2009
iBotnet: Researchers find signs of zombie Macs
Writing in the current issue of Virus Bulletin (subscription required), researchers Mario Ballano Barcena and Alfredo Pesoli found two malware variants — OSX.Iservice and OSX.Iservice.B — using different techniques to obtain the user’s password and take control of the infected Mac machine."
Read the full ZD Net article
Tuesday, March 31, 2009
Help Your PC Friends Through The Conficker Virus/Worm Tomorrow
Continue Reading
Monday, March 30, 2009
Apple Mac malware: caught on camera
Oh, and Windows users shouldn't feel too smug about this either. If you visit the site on a Windows computer, it will serve up a malicious Windows executable from the Zlob family of malware rather than a Mac OS X Trojan horse."
This attack does not depend on any browser vulnerabilities - it works by the user being convinced via social engineering that this is a program that they would like to run on their computer.
read more | digg story